Believe it or not it’s around seven years since Windows 10 was first release onto the world and it’s has come a long way, especially in the area of updates. Here’s a Microsoft Mechanics video that was released in early 2017 that provides an overview of Windows as a Service (WaaS). Remember that this was a few years ago so it’s not really up-to-date but does demonstrate the principle which haven’t really changed.
“It’s about making money right?” Well yes however I still think its a better enterprise solution. WaaS is about two simple concepts (and this is a cynical view but i think accurate):- To reduce the volume and complexity of support cases that MS have to deal with as a result of bespoke environments.
- To enable the standardisation and simplification of customer environments to ensure compatibility with Azure and O365 (this is the money maker).
As a result of these two concepts there are many benefits to the enterprise however, it comes at a cost. Firstly (and most obvious) you need subscription based licences for Windows, gone are the days of one-time-cost licences. Second and more problematic is the hardware cost associated with WaaS. Without going down the rabbit hole of Windows 11 not being supported on some hardware (subject of a future post :smilie:), Microsoft guarantees to provide hardware driver support for three years. Initially most admins will say ‘..that’s fine, the Hardware provider offers seven years..’, which is ok but that means you have to deploy drivers to an affected device, which could be problematic during Autopilot depending on which bit of hardware is affected. The easy solution is to have a hardware lifecycle of three years but how many enterprises can afford that?!
Anyway, back to the point; Microsoft is a for profit organisation and the subscription based model for services is well known to be the best growth model that exists, hence its proliferation in all things digital. While this is a very cynical view, I’m by no means saying its a bad thing. As an IT Pro, the WaaS model is vastly simpler to build and support and enables significant gains in the simplification of an Enterprise (I’ve seen estates of 20,000+ endpoints managed by 2 support engineers on a 8-6 basis). Yes there’s an argument that the Microsoft direction of travel in the last five years has been nothing more than an exercise in making money and growing its market position but do you blame them?
I’ll explore the unseen costs of WaaS in a future post.
“So why is this approach better…” From the Enterprise perspective, why would you not want a simplified environment that’s much easier to support, with less people and is more resilient to attack or failure? Don’t get me wrong there are some very complex subjects to grasp when implementing WaaS (I’m looking at you WDAC as well as you reverse differential compression!) however, you don’t have to understand these things to be able to implement and use them (although it does help with planning).
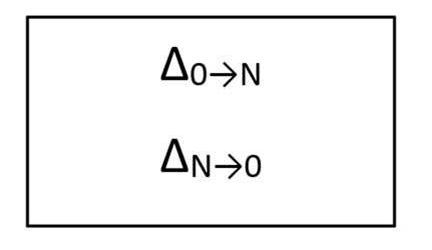
One of the major simplifications that has been made within Windows 10 updates is the fact that you no longer choose which updates you can apply with regard to monthly patches. Now the device receives one patch which brings it up to date regardless of the last time it was updated. We’ll get into this subject in a little more detail in the next post but simply, a monthly patch returns the OS to the RTM (release to market - version 0) state and then applies the most recent changes to that codebase. In effect, the device has RTM plus this months patch. This means the all devices maintain the same level of update status (assuming they all have this months patch) which from a support perspective can only be a good thing.
What do we mean by update/upgrade? For the sake of simplicity, we’ll be discussing two update types:
- Cumulative Updates These are released Monthly (second Tuesday). Previously, the IT function could decide which monthly patches to apply and which to miss out, this is no longer possible as all quality updates are mandatory. While it’s possible to delay the release, any subsequent patches include the previous released code changes, ensuring that all devices remain up to date.
- Feature Updates - These are the upgrades to the next version of W1O and are obviously larger than Cumulative Updates. The release process however is no different other than the timeline being extended i.e. the quality update release process lasts around a month whereas the Feature Release process is likely to be over several weeks. There are a few other types as well e.g. delivered as upgrades to applications (did you know that the Windows Calculator was a stand-alone application, as is the Start menu?). I’ll discuss these another time as to do so here will just confuse matters.
Feature updates vs LTSC So while it’s obvious monthly security patches are a necessity, what about Feature Updates - are these a good idea for an Enterprise? In short yes, they’re a great idea! Upgrading to the latest version of the OS has always been a challenge for and Enterprise however the most organisations take on that challenge in order to deliver more productivity to their end users. There is frequently a fear of upgrading generally caused by the amount of effort required and all the resources needed to implement - we love those 18 month projects in IT :smile:.
I’ve recently seen one approach where the client implemented an LTSC (long term service channel) version of Windows 10. While this generally worked and the estate was managed using SCCM as it normally would be, there were some minor compromises to the user experience. We found that co-management (with Intune) was very hit-and-miss with the LTSC version and more problematic, you essentially have to rebuild the device in order to get back into the enterprise service channel. The LTSC version definitely has its place but in my opinion, that’s not as a general end user OS.
Solving the rollout problem So how do you solve the rollout problem of changing to the next OS version without launching a big upgrade project every year? We use in place upgrades with deployment rings. To simplify, think of deployment rings as a collection AD groups that your devices reside in. The general advice is a minimum of three rings and a maximum of seven.
To provide an example:
| Ring | Function/Members |
|---|---|
| 1 | Contains a few test devices that will always be on a preview version of the OS |
| 2 | Contains your pilot users - those that will try the OS before everyone else |
| 3 | Contains the bulk of your estate |
| 4 | Contains the critical devices that need to be protected against failure/bugs |
We use the rings as barriers, to limit the blast radius of any issues they found during the roll out process. Early issues should be ironed out in the first two rings, before subjecting the bulk of your estate to the upgrade. Note we also use the deployment rings for the monthly patch roll out, again to limit the blast radius of any issues (not that Microsoft ever releases dodgy code :wink:). At this point I usually hear ‘..but managing which device goes in which group is a huge amount of effort..’ to which my usual response is ‘..true if you do it manually..’. Think about extension attributes and dynamic groups - i’ll do a post on this at some point as it’s very simple to do but not necessarily obvious.
With regard to in place upgrades, the majority of you will have likely used SCCM to deploy task sequence based upgrades however, what often works better with Windows 10 (especially for a hybrid workforce )is the use of Windows Update for Business (WUfB). This free service essentially assesses a device to understand its current state for both cumulative and feature updates, and then offers the latest versions to the device via the CDN. Ideally your endpoints will talk directly to WUfB without the traffic being proxied as this simplifies and speeds up the delivery process. We’ll go into a little more detail on this in the Delivery Optimization post.
“The language of WaaS” Now lets cover a little off the language and abbreviations we’ll be using in this series, just so your armed. Microsoft are famous for changing the name of things (and in some cases not changing it when it definitely should be) and so I thought it a good idea to give you a bit of a breakdown of some of the more frequently used terminology.
| Abbreviation | Value | Description |
|---|---|---|
| WaaS | Windows as a Service | (Surprise!) this is the name given to the collection of tools and services we’ve been discussing. |
| WUfB | Windows Update for Business | The free service that pushes updates/upgrades to your endpoints. |
| AAD | Azure Active Directory | Your cloud based Active Directory. |
| MDM | Mobile device management | The tool you use to administer your endpoints e.g. Configuration Manager, Intune etc |
| DO | Delivery Optimisation | Another free service that tracks all your devices and what state (upgrade/patch level) they are in. |
That’s it for the brief background of WaaS. In the next part we’ll discuss how size matters when it comes to updates in an Enterprise network and how we avoid clogging up the network with constant updates. Thanks for reading so far, hopefully the rest of the series will prove interesting for you.
As always, feel free to reach out if you need a little help.